Security Maturity Model
Home » Security Maturity Model
Security Maturity Model: Practitioner’s Guide
-
- Home
- Pages
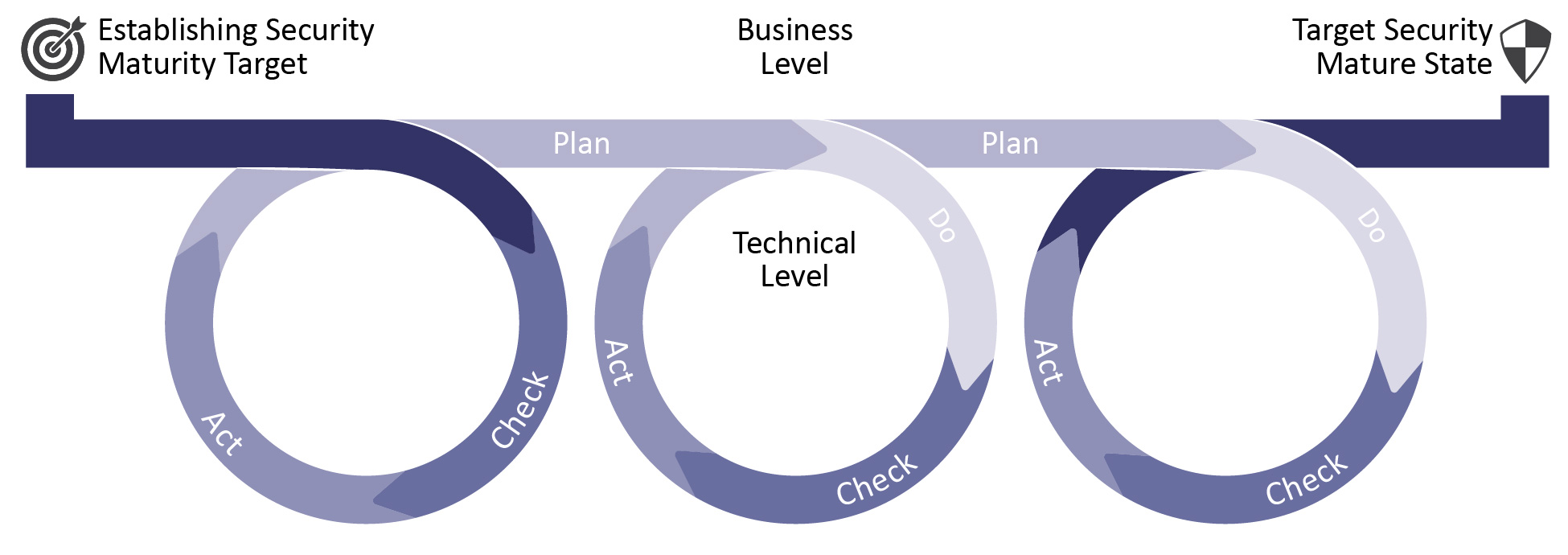 The cybersecurity landscape is complex and ever-changing. Deciding where to focus security resources can be a challenge. Security maturity modeling provides a path for communicating with business stakeholders and a strategic step to attaining the necessary support to move forward with a comprehensive security roadmap.
The Internet of Things (IoT) Security Maturity Model (SMM) builds on the concepts identified in the Industrial Internet Security Framework (IISF) and provides a path for IoT providers to understand where they need to be, make intelligent choices about which mechanisms to use and how to invest in the mechanisms to meet their needs. Cybersecurity experts representing the Industry IoT Consortium Security Working Group have developed the IoT SMM: Practitioner's Guide to extend the value of the SMM and assist stakeholders in the assessment process.
The cybersecurity landscape is complex and ever-changing. Deciding where to focus security resources can be a challenge. Security maturity modeling provides a path for communicating with business stakeholders and a strategic step to attaining the necessary support to move forward with a comprehensive security roadmap.
The Internet of Things (IoT) Security Maturity Model (SMM) builds on the concepts identified in the Industrial Internet Security Framework (IISF) and provides a path for IoT providers to understand where they need to be, make intelligent choices about which mechanisms to use and how to invest in the mechanisms to meet their needs. Cybersecurity experts representing the Industry IoT Consortium Security Working Group have developed the IoT SMM: Practitioner's Guide to extend the value of the SMM and assist stakeholders in the assessment process.
IoT SMM: Description And Intended Use White Paper
The IoT Security Maturity Model Description and Intended Use White Paper is intended for owners of IoT systems, decision makers, security leaders in various verticals, business risk managers, system integrators, architects, security assessors, analysts, policy and regulatory authorities, and other stakeholders. It provides an overview of the purpose and need and introduces the SMM model. This model enables stakeholders to make strategic decisions on where to invest to implement security practices appropriate to the needs and constraints of the specific IoT system. This document is followed by the SMM Practitioner's Guide which offers greater detail.IoT SMM: Practitioner's guide
The Practitioner's Guide provides a pragmatic approach, enabling implementation teams to communicate an IoT system's current state of security through confident discussions with business stakeholders about the desired state of security maturity, where gaps exist and a roadmap for achieving their goal. The Practitioner's Guide describes how to reach a given security comprehensiveness for each security domain, subdomain and practice and can be extended to address specific industry or system scope needs. Various industry use case examples demonstrate how an organization might select a target state or evaluate a current state.Primary Authors
- Sandy Carielli - Entrust Datacard
- Matthew Eble - Praetorian
- Frederick Hirsch - Fujitsu
- Ekaterina Rudina - Kaspersky Lab
- Ron Zahavi - Microsoft Azure IoT
Other Contributors
- James Clardy - Tata Consultancy Services / NetFoundry
- Marcellus Buchheit - Wibu-Systems
- Steve Clark - WISeKey